- SIP — Messaging
- Request Methods
- Core Methods
- INVITE
- INVITE Example
- BYE
- REGISTER
- CANCEL
- ACK
- OPTIONS
- Extension Methods
- Subscribe
- NOTIFY
- PUBLISH
- REFER
- INFO
- UPDATE
- PRACK
- MESSAGE
- Click Verify to check if bitovka.site is legit website or scam website
- URL checker is a free tool to detect malicious URLs including malware, scam and phishing links Get a complete analysis of bitovka.site the check if the website is legit or scam.
- Click Verify to check if bitovka.site is legit or a phishing or scam website
- Webpage Details
- Register Information
- Registrant Contact
- Technical Contact
- Administrative Contact
- Domain Email Servers
- Domain Info
- Reverse IP
- Geolocation
- Recent queries
- Free tools
- FAQ & Answers
SIP — Messaging
SIP messages are of two types − requests and responses.
- The opening line of a request contains a method that defines the request, and a Request-URI that defines where the request is to be sent.
- Similarly, the opening line of a response contains a response code.
Request Methods
SIP requests are the codes used to establish a communication. To complement them, there are SIP responses that generally indicate whether a request succeeded or failed.
These SIP requests which are known as METHODS make SIP message workable.
- METHODS can be regarded as SIP requests, since they request a specific action to be taken by another user agent or server.
- METHODS are distinguished into two types −
- Core Methods
- Extension Methods
Core Methods
There are six core methods as discussed below.
INVITE
INVITE is used to initiate a session with a user agent. In other words, an INVITE method is used to establish a media session between the user agents.
- INVITE can contain the media information of the caller in the message body.
- A session is considered established if an INVITE has received a success response(2xx) or an ACK has been sent.
- A successful INVITE request establishes a dialog between the two user agents which continues until a BYE is sent to terminate the session.
- An INVITE sent within an established dialog is known as a re-INVITE.
- Re-INVITE is used to change the session characteristics or refresh the state of a dialog.
INVITE Example
The following code shows how INVITE is used.
INVITE sips:Bob@TMC.com SIP/2.0 Via: SIP/2.0/TLS client.ANC.com:5061;branch = z9hG4bK74bf9 Max-Forwards: 70 From: Alice;tag = 1234567 To: Bob Call-ID: 12345601@192.168.2.1 CSeq: 1 INVITE Contact: Allow: INVITE, ACK, CANCEL, OPTIONS, BYE, REFER, NOTIFY Supported: replaces Content-Type: application/sdp Content-Length: . v = 0 o = Alice 2890844526 2890844526 IN IP4 client.ANC.com s = Session SDP c = IN IP4 client.ANC.com t = 3034423619 0 m = audio 49170 RTP/AVP 0 a = rtpmap:0 PCMU/8000
BYE
BYE is the method used to terminate an established session. This is a SIP request that can be sent by either the caller or the callee to end a session.
- It cannot be sent by a proxy server.
- BYE request normally routes end to end, bypassing the proxy server.
- BYE cannot be sent to a pending an INVITE or an unestablished session.
REGISTER
REGISTER request performs the registration of a user agent. This request is sent by a user agent to a registrar server.
- The REGISTER request may be forwarded or proxied until it reaches an authoritative registrar of the specified domain.
- It carries the AOR (Address of Record) in the To header of the user that is being registered.
- REGISTER request contains the time period (3600sec).
- One user agent can send a REGISTER request on behalf of another user agent. This is known as third-party registration. Here, the From tag contains the URI of the party submitting the registration on behalf of the party identified in the To header.
CANCEL
CANCEL is used to terminate a session which is not established. User agents use this request to cancel a pending call attempt initiated earlier.
- It can be sent either by a user agent or a proxy server.
- CANCEL is a hop by hop request, i.e., it goes through the elements between the user agent and receives the response generated by the next stateful element.
ACK
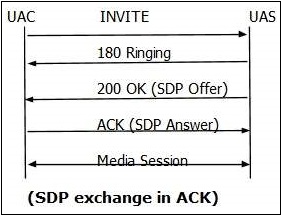
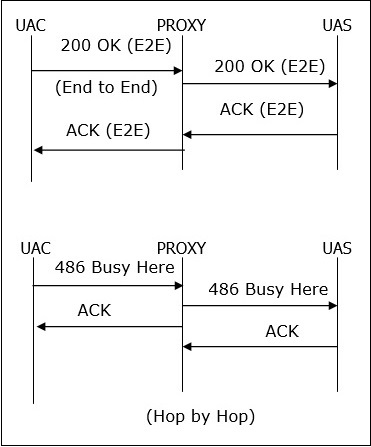
ACK is used to acknowledge the final responses to an INVITE method. An ACK always goes in the direction of INVITE.ACK may contain SDP body (media characteristics), if it is not available in INVITE.
- ACK may not be used to modify the media description that has already been sent in the initial INVITE.
- A stateful proxy receiving an ACK must determine whether or not the ACK should be forwarded downstream to another proxy or user agent.
- For 2xx responses, ACK is end to end, but for all other final responses, it works on hop by hop basis when stateful proxies are involved.
OPTIONS
OPTIONS method is used to query a user agent or a proxy server about its capabilities and discover its current availability. The response to a request lists the capabilities of the user agent or server. A proxy never generates an OPTIONS request.
Extension Methods
Subscribe
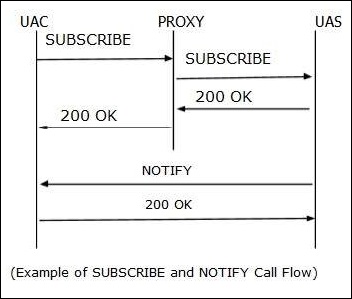
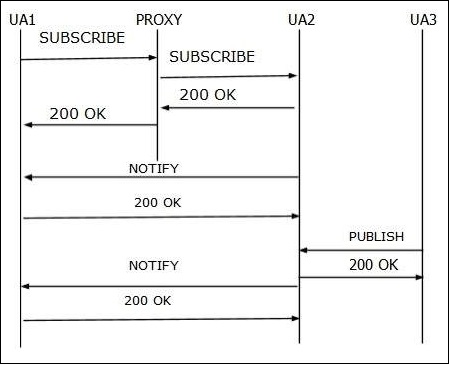
SUBSCRIBE is used by user agents to establish a subscription for the purpose of getting notification about a particular event.
- It contains an Expires header field that indicates the duration of a subscription.
- After the time period passes, the subscription will automatically terminate.
- Subscription establishes a dialog between the user agents.
- You can re-subscription again by sending another SUBSCRIBE within the dialog before the expiration time.
- A 200 OK will be received for a subscription from User.
- Users can unsubscribe by sending another SUBSCRIBE method with Expires value 0(zero).
NOTIFY
NOTIFY is used by user agents to get the occurrence of a particular event. Usually a NOTIFY will trigger within a dialog when a subscription exists between the subscriber and the notifier.
- Every NOTIFY will get 200 OK response if it is received by notifier.
- NOTIFY contain an Event header field indicating the event and a subscriptionstate header field indicating the current state of the subscription.
- A NOTIFY is always sent at the start and termination of a subscription.
PUBLISH
PUBLISH is used by a user agent to send event state information to a server.
- PUBLISH is mostly useful when there are multiple sources of event information.
- A PUBLISH request is similar to a NOTIFY, except that it is not sent in a dialog.
- A PUBLISH request must contain an Expires header field and a Min-Expires header field.
REFER
REFER is used by a user agent to refer another user agent to access a URI for the dialog.
- REFER must contain a Refer-To header. This is a mandatory header for REFER.
- REFER can be sent inside or outside a dialog.
- A 202 Accepted will trigger a REFER request which indicates that other user agent has accepted the reference.
INFO
INFO is used by a user agent to send call signalling information to another user agent with which it has established a media session.
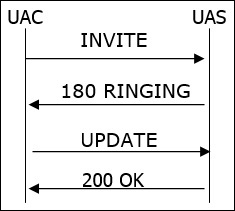
UPDATE
UPDATE is used to modify the state of a session if a session is not established. User could change the codec with UPDATE.
IF a session is established, a re-Invite is used to change/update the session.
PRACK
PRACK is used to acknowledge the receipt of a reliable transfer of provisional response (1XX).
- Generally PRACK is generated by a client when it receive a provisional response containing an RSeq reliable sequence number and a supported:100rel header.
- PRACK contains (RSeq + CSeq) value in the rack header.
- The PRACK method applies to all provisional responses except the 100 Trying response, which is never reliably transported.
- A PRACK may contain a message body; it may be used for offer/answer exchange.
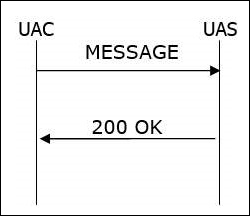
MESSAGE
It is used to send an instant message using SIP. An IM usually consists of short messages exchanged in real time by participants engaged in text conversation.
- MESSAGE can be sent within a dialog or outside a dialog.
- The contents of a MESSAGE are carried in the message body as a MIME attachment.
- A 200 OK response is normally received to indicate that the message has been delivered at its destination.
Click Verify to check if bitovka.site is legit website or scam website
URL checker is a free tool to detect malicious URLs including malware, scam and phishing links
Get a complete analysis of bitovka.site the check if the website is legit or scam.Click Verify to check if bitovka.site is legit or a phishing or scam website
If you like this tool, please share.
Webpage Details
Register Information
Registrant Contact
Technical Contact
Administrative Contact
Domain Email Servers
Domain Info
Reverse IP
Geolocation
Recent queries
Free tools
Check a complete list of our free tools
FAQ & Answers
URL Checker uses advanced artificial intelligence (AI) and machine learning techniques to quickly detect scam websites and determine whether a website is legit.
Often, you want to visit a website for various reasons, but you are unsure whether to trust the website. You are asking yourself questions such as “is this website legit?” or “is it a scam website?” or “is this a safe website?” or “is this site real?” and so many similar questions. URL checker is an intelligent scam detector which analyses website link characteristics and allows finding out proactively and swiftly whether by clicking on the link you will land on an unsafe website or a website that is safe. It helps with website credibility check and verifying whether a company is legit.
Using URL checker for fraudulent websites check or to check whether a website is safe is very easy. Go to the URL checker webpage at https://www.emailveritas.com/url-checker enter the link in the search box and click the Search icon. URL checker will check the website link and quickly displays its results as whether this is a scam website or a safe website.
URL Checker is a safe link checker which uses advanced artificial intelligence and natural language processing techniques to analyze website link characteristics and check the credibility of the company owning it.
A scam detector checks a website for scams, checks the reputation and credibility of the site, and verifies whether the company owning the site is legit.
Website legit checker helps quickly finding out whether a link you are about to click or a website you are about to visit is unsafe or devoid of scams.
Website legit checker helps spot malicious, scam and fraudulent sites. Scam websites infect your devices with malware, compromise your identity, and steal your credit card and online banking information.
Website legit checker uses advanced artificial intelligence and machine learning to verify whether a website is legit or a scam.
Using website legit checker is easy. Go to the URL checker webpage at https://www.emailveritas.com/url-checker type the link in the search box and click the Search icon. URL checker will check whether the link is safe and quickly display the results.
Assuring Genuine and safe electronic messaging
Email Veritas is a cybersecurity company dedicated to developing anti-phishing tools and have as a mission to create a more secure digital world through a tool for protecting corporate e-mails, Assuring Genuine and Safe Electronic Messaging. Our team of scientists have experience and deep knowledge of Computer Security and Artificial Intelligence (AI).