- Saved searches
- Use saved searches to filter your results more quickly
- adbrsln/RBAC-php
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- PHP-RBAC
- Why RBAC?
- What is RBAC?
- Continue.
- Saved searches
- Use saved searches to filter your results more quickly
- License
- hamza1886/role-based-access-control
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
- Simple role based access control example using PHP and MYSQLi
- What I am going to do:
- Admin Template Link:
- Folder Structure:
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Role Based Access Control php framework
adbrsln/RBAC-php
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Role Based Access Control PHP Framework
Role Based Access Control PHP Framework is my personal PHP script in order to develop a rapid system/application mainly focusing on login and verify user access control process. this php script equipped with md5 hashing for small scale system (you may used any type of hashing you desired). This script already has the required file structure to jumpstart you system development.
Explaination of the columns in the users table
- id : unique value of the user data
- email : email of the user
- password : password of the user (MD5 Hash)
- name : name of the user
- userType : type of the user. determined by Int such as 1 for admin, 2 for user , 3 for accountant
- import the rbac.sql into your mysql database.
- Copy all the project items
- The file structure is easy to use and understand. admin, user and accountant is the type of the user in your system.
- configure the database credentials and configuration details in the ‘includes/config.php’
- if there’s no user available in the database, run this sql below
INSERT INTO `user` (`id`, `email`, `password`, `name`, `userType`) VALUES (57, 'admin@email.com', 'ee11cbb19052e40b07aac0ca060c23ee', 'Muhammad Farid', 1), (58, 'user@email.com', 'ee11cbb19052e40b07aac0ca060c23ee', 'Muhammad Farid', 2,), (59, 'accountant@email.com', 'ee11cbb19052e40b07aac0ca060c23ee', 'Muhammad Farid', 3); PHP-RBAC
PHP-RBAC is the de-facto authorization library for PHP. It provides developers with NIST Level 2 Standard Role Based Access Control and more, in the fastest implementation yet.
Why RBAC?
Role Based Access Control is the standard means of authorization (access control). The other approach is ACLs, where a table defines who can do what. ACLs are only good for very small systems, because of the following reasons:
Big systems have lots of permits
People move in organizations, and all their permits should be changed when they do
Maintenance (adding, changing, removing) of 100,000 permits requires a handful of staff
Maintenance of the permits assigned to each user, requires more staff than above!
One wrong user-permit and you have a serious breach in your security, so no room for error
Example of an ACL
Usage of ACLs has led to broken authorization and access control all over applications, and authorization is limited only to critical operations to keep number of permits low.
But RBAC is here to save the day.
What is RBAC?
RBAC separates the concepts of Users, Roles and Permissions. Roles are defined in a system, then Permissions defined separately. Then the security administrator decides what role should be permitted to do what action, by assigning that role to the permission. Finally users are assigned to roles. The system does the rest.
Still lots of permits in the system are the problem
People move, and only their roles need to be changed
Maintenance of permits is still an issue
Maintenance of permits assigned to each role is easy, it doesn’t change much logically.
Role-Permission assignments can be double checked so that no wrong permit is given to any role
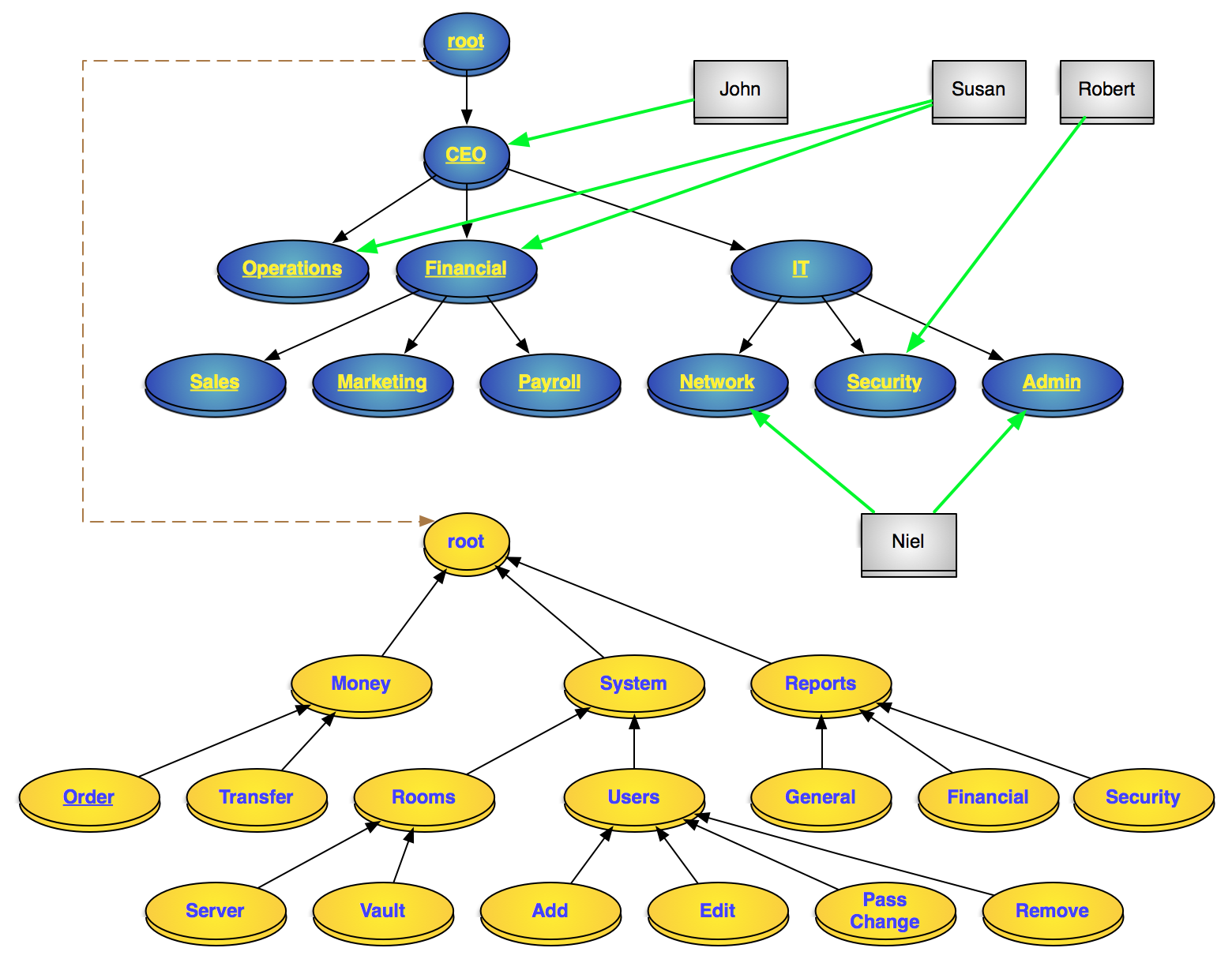
That was NIST Level 1 standard RBAC above, and it still had issues. NIST Level 2 RBAC requires Roles and/or Permissions to be hierarchical, so that management of them can easily be handled in hierarchies. The figure below demonstrates a system in hierarchical RBAC:
A hierarchical RBAC model of a system
Blue: roles, Gray: users, Yellow: permissions
Continue.
You are now ready for the next step: Before you begin
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Implementation of Role-Based Access Control in PHP
License
hamza1886/role-based-access-control
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Implementation of Role Based Access Control in PHP
Open Source web-based implementation of Role Based Access Control (RBAC) in PHP. The implementation is flexible to integrate into any existing PHP project.
Characteristics and Policies [1]
- within the RBAC framework, a user is a person, a role is a collection of job functions, and an operation represents a particular mode of access to a set of one or more protected RBAC objects;
- the type of operations and the objects that RBAC controls is dependent on the type of system in which it will be implemented, e.g. within a transaction management system, operations would take the form of and exhibit all the properties of a transaction;
- roles can have overlapping responsibilities and privileges, i.e. users belonging to different roles may need to perform common operations. RBAC therefore supports the concept of role hierarchies;
- a role hierarchy defines roles that have unique attributes and that may contain other roles, i.e. that one role may implicitly include the operations, constraints, and objects that are associated with another role;
- role authorisation (association of user with a role) can be subject to the following:
- the user can be given no more privilege than is necessary to perform his/her job (principle of least privilege);
- the role in which the user is gaining membership is not mutually exclusive with another role for which the user already possesses membership (static separation of duty); &
- the numerical limitation that exists for role membership cannot be exceeded (cardinality property);
- the user is authorised for the role being proposed for activation;
- the activation of the proposed role is not mutually exclusive with any other active role(s) of the user;
- the proposed operation is authorised for the role that is being proposed for activation; &
- the operation being proposed is consistent within a mandatory sequence of operations;
- the role is part of the subjects current active role set;
- the role is allowed to perform the operation; &
- the operation to access the object is authorised.
Database Four database tables are created to store role and permission information: the roles table stores a role ID and role name, the permissions table stores a permission ID and description, the role_perm table associates which permissions belong to which roles, and the user_role table associates which roles are assigned to which users.
Model Classes Role class is to return a role object that is populated with each roles corresponding permissions. PrivilegedUser class extends existing User class (reuse existing code logic for managing users) and then add some additional methods specifically working with privileges. Permission class is to add and delete permissions. Database class to connect with database.
Password Passwords are stored using 128-bit SHA512 algorithm. The algorithm is considered computationally expensive to brute-force password (in the event your database is compromised).
1. Create empty database tables using db/schema.sql then insert values in roles , permissions , role_perm and user_role tables. Alternatively, sample working database tables are also available db/schema-sample.sql .
2. Run web server.
Usage: -S : -t
Example: C:\php\php.exe -S 127.0.0.1:82 -t C:\role_based_access_control\3. Browser visit to http://127.0.0.1:82.
[1]: A. Rhodes and W. Caelli, «A Review Paper — Role Based Access Control», pp. 3-5.Copyright (c) 2017 Hamza Rashid Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.About
Implementation of Role-Based Access Control in PHP
Simple role based access control example using PHP and MYSQLi
Role based user access control is one of the most significant feature of modern systems. Because its restrict user to show unnecessary information. User access control shows relevant information to user. Only admin or super user has all the rights to see, insert, update and delete information from system.
If I talk about wordpress, it has 4 major user roles which are Administrator, Editor, Author and Contributor. All 4 have different behaviors and access control but administrator user has all the rights in wordpress. User with this role can do anything from writing post to delete post, add theme to delete theme, add user to delete user.
So in this post I will create simple role based access control using php and mysqli.My purpose is to give you an idea about how these types of system develop and I hope this post will be going to help you in your future development.
What I am going to do:
I will create wordpress like user access level in which I will hide and show menu items according to user role.For this I will store user data into session.I will use login and inner page of free html5 bootstrap admin template. I will also break inner page into multiple php files like header, footer, and sidebar.
Admin Template Link:
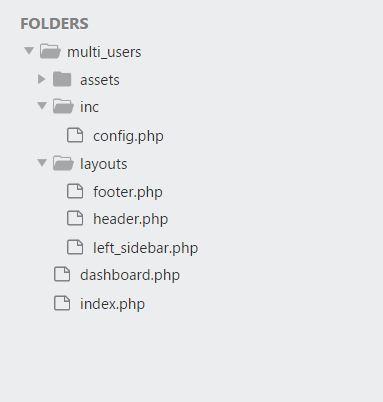
Folder Structure:
File/Folder Description Index.php This is a login page Dashboard.php After successful login, User will land on this page. Assets Folder This folder has css, js, bootstarp and plugins file Inc Folder This folder has config.php file in which there is a database connection and getUserAccessRoleByID() function. Layouts Folder This folder has 3 files footer.php, header,left_sidebar.php. I split static content of admin template in these files.
 Big systems have lots of permits
Big systems have lots of permits
 People move, and only their roles need to be changed
People move, and only their roles need to be changed