- openssl_x509_read
- Parameters
- Return Values
- Changelog
- User Contributed Notes 3 notes
- Как прочитать SSL сертификат из PHP
- Результат:
- Вывод основных данных
- Saved searches
- Use saved searches to filter your results more quickly
- License
- joelwmale/php-ssl-certificate
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
openssl_x509_read
openssl_x509_read() parses the certificate supplied by certificate and returns an OpenSSLCertificate object for it.
Parameters
X509 certificate. See Key/Certificate parameters for a list of valid values.
Return Values
Returns an OpenSSLCertificate on success or false on failure.
Changelog
| Version | Description |
|---|---|
| 8.0.0 | On success, this function returns an OpenSSLCertificate instance now; previously, a resource of type OpenSSL X.509 was returned. |
| 8.0.0 | certificate accepts an OpenSSLCertificate instance now; previously, a resource of type OpenSSL X.509 was accepted. |
User Contributed Notes 3 notes
To get the real timestamps as integer values for the validity daterange you can use as follows:
$data = openssl_x509_parse ( file_get_contents ( ‘/path/to/cert.crt’ ));
$validFrom = date ( ‘Y-m-d H:i:s’ , $data [ ‘validFrom_time_t’ ]);
$validTo ) date ( ‘Y-m-d H:i:s’ , $data [ ‘validTo_time_t’ ]);
echo $validFrom . «\n» ;
echo $validTo . «\n» ;
After some tests I’ve been able to get some results this way .
$fp = fopen ( «/etc/httpd/conf/ssl/moncertif.crt» , «r» );
$cert = fread ( $fp , 8192 );
fclose ( $fp );
echo «Read
» ;
echo openssl_x509_read ( $cert );
echo «
» ;
echo «*********************» ;
echo «
» ;
echo «Parse
» ;
print_r ( openssl_x509_parse ( $cert ));
/*
// or
print_r(openssl_x509_parse( openssl_x509_read($cert) ) );
*/
Short HOWTO for getting data out of a client certificate via an SSL enabled iPlanet (Netscape Enterprise or Sun ONE) web server.
The iPlanet server sets $_SERVER[«CLIENT_CERT»] whenever a client authenticates with a certificate. This variable contains an encoded representation of the certificate presented by the client. This in itself is useless to scripts or applications, we need to extract the actual information from the encoding. It turns out that we are in luck, the encoding is NEARLY a standard PEM encoding which can be read by the openssl_x509_read() function. A standard PEM has a begin line, an end line and inbetween is a base64 encoding of the DER representation of the certificate. PEM requires that linefeeds be present every 64 characters, however this is already the case with our CLIENT_CERT variable. For some reason the iPlanet server neglects to attach the begin and end headers, all that is required to allow access to the certificate is replacing these headers. Here is a small code excerpt for doing just that and printing out the raw certificate data.
$beginpem = «——BEGIN CERTIFICATE——\n» ;
$endpem = «——END CERTIFICATE——\n» ;
// Small function to print the data recursivly.
function print_element ( $item , $key )
if( is_array ( $item ) )
echo » $key is Array:\n» ;
array_walk ( $item , ‘print_element’ );
echo » $key done\n» ;
>
else
echo » $key = $item \n» ;
>
// Build the PEM string.
$pemdata = $beginpem . $_SERVER [ «CLIENT_CERT» ]. «\n» . $endpem ;
// Get a certificate resource from the PEM string.
$cert = openssl_x509_read ( $pemdata );
// Parse the resource and print out the contents.
$cert_data = openssl_x509_parse ( $cert );
array_walk ( $cert_data , ‘print_element’ );
// Free the resource
openssl_x509_free ( $cert );
?>
- OpenSSL Functions
- openssl_cipher_iv_length
- openssl_cipher_key_length
- openssl_cms_decrypt
- openssl_cms_encrypt
- openssl_cms_read
- openssl_cms_sign
- openssl_cms_verify
- openssl_csr_export_to_file
- openssl_csr_export
- openssl_csr_get_public_key
- openssl_csr_get_subject
- openssl_csr_new
- openssl_csr_sign
- openssl_decrypt
- openssl_dh_compute_key
- openssl_digest
- openssl_encrypt
- openssl_error_string
- openssl_free_key
- openssl_get_cert_locations
- openssl_get_cipher_methods
- openssl_get_curve_names
- openssl_get_md_methods
- openssl_get_privatekey
- openssl_get_publickey
- openssl_open
- openssl_pbkdf2
- openssl_pkcs12_export_to_file
- openssl_pkcs12_export
- openssl_pkcs12_read
- openssl_pkcs7_decrypt
- openssl_pkcs7_encrypt
- openssl_pkcs7_read
- openssl_pkcs7_sign
- openssl_pkcs7_verify
- openssl_pkey_derive
- openssl_pkey_export_to_file
- openssl_pkey_export
- openssl_pkey_free
- openssl_pkey_get_details
- openssl_pkey_get_private
- openssl_pkey_get_public
- openssl_pkey_new
- openssl_private_decrypt
- openssl_private_encrypt
- openssl_public_decrypt
- openssl_public_encrypt
- openssl_random_pseudo_bytes
- openssl_seal
- openssl_sign
- openssl_spki_export_challenge
- openssl_spki_export
- openssl_spki_new
- openssl_spki_verify
- openssl_verify
- openssl_x509_check_private_key
- openssl_x509_checkpurpose
- openssl_x509_export_to_file
- openssl_x509_export
- openssl_x509_fingerprint
- openssl_x509_free
- openssl_x509_parse
- openssl_x509_read
- openssl_x509_verify
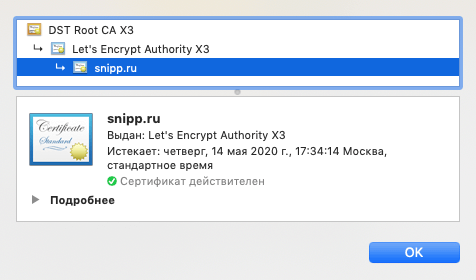
Как прочитать SSL сертификат из PHP
SSL сертификат можно получить с помощью контекста потоков (Stream Context), а разобрать его поможет функция openssl_x509_parse() . Если сертификат отсутствует или просрочен, то код ошибки и текст будет в переменных $err_no и $err_str .
$url = 'ssl://snipp.ru:443'; $context = stream_context_create( array( 'ssl' => array( 'capture_peer_cert' => true, 'verify_peer' => false, // Т.к. промежуточный сертификат может отсутствовать, 'verify_peer_name' => false // отключение его проверки. ) ) ); $fp = stream_socket_client($url, $err_no, $err_str, 30, STREAM_CLIENT_CONNECT, $context); $cert = stream_context_get_params($fp); if (empty($err_no))
Результат:
Array( [name] => /CN=snipp.ru [subject] => Array( [CN] => snipp.ru ) [hash] => d29c8ea7 [issuer] => Array( [C] => US [O] => Let's Encrypt [CN] => Let's Encrypt Authority X3 ) [version] => 2 [serialNumber] => 295366585736462130072577585684820136690675 [serialNumberHex] => 0364011F3441AE879CE07F8A1018FDFA03F3 [validFrom] => 200214143414Z [validTo] => 200514143414Z [validFrom_time_t] => 1581690854 [validTo_time_t] => 1589466854 [signatureTypeSN] => RSA-SHA256 [signatureTypeLN] => sha256WithRSAEncryption [signatureTypeNID] => 668 [purposes] => Array( [1] => Array( [0] => 1 [1] => [2] => sslclient ) [2] => Array( [0] => 1 [1] => [2] => sslserver ) [3] => Array( [0] => 1 [1] => [2] => nssslserver ) [4] => Array( [0] => [1] => [2] => smimesign ) [5] => Array( [0] => [1] => [2] => smimeencrypt ) [6] => Array( [0] => [1] => [2] => crlsign ) [7] => Array( [0] => 1 [1] => 1 [2] => any ) [8] => Array( [0] => 1 [1] => [2] => ocsphelper ) [9] => Array( [0] => [1] => [2] => timestampsign ) ) [extensions] => Array( Php get https certificate => Digital Signature, Key Encipherment [extendedKeyUsage] => TLS Web Server Authentication, TLS Web Client Authentication [basicConstraints] => CA:FALSE [subjectKeyIdentifier] => 93:5E:0E:54:E4:68:87:51:61:07:15:45:04:76:EB:AC:53:69:00:AE [authorityKeyIdentifier] => keyid:A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1 [authorityInfoAccess] => OCSP - URI:http://ocsp.int-x3.letsencrypt.org CA Issuers - URI:http://cert.int-x3.letsencrypt.org/ [subjectAltName] => DNS:snipp.ru, DNS:www.snipp.ru [certificatePolicies] => Policy: 2.23.140.1.2.1 Policy: 1.3.6.1.4.1.44947.1.1.1 CPS: http://cps.letsencrypt.org ) )Вывод основных данных
echo 'Домен: ' . $info['subject']['CN'] . "\r\n"; echo 'Выдан: ' . $info['issuer']['CN'] . "\r\n"; echo 'Истекает: ' . date('d.m.Y H:i', $info['validTo_time_t']);Домен: snipp.ru Выдан: Let's Encrypt Authority X3 Истекает: 14.05.2020 17:34Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Easily retrieve the ssl certificate for any host
License
joelwmale/php-ssl-certificate
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Easily retrieve the ssl certificate for any host
This package makes it easy to download a certificate for a host.
use Joelwmale\SslCertificate\Certificate; $certificate = Certificate::forHost('joelmale.com');
You can install the package via composer:
composer require joelwmale/php-ssl-certificate
Available Properties & Methods
/** @var string */ $certificate->issuer; // returns the issuer of the certificate /** @var string */ $certificate->domain; // returns the primary domain on the certificate /** @var array */ $certificate->additionalDomains; // returns all the additional/alt domains on the certificate /** @var bool */ $certificate->isValid; // returns true if valid, false if not /** @var Carbon */ $certificate->issued; // returns a carbon instance of when the certificate was issued /** @var Carbon */ $certificate->expires; // returns a carbon instance of when the certificate expires /** @var int */ $certificate->expiresIn; // returns the amount of days until the certificate expires /** @var bool */ $certificate->expired; // returns true if the certificate is expired, false if not /** @var string */ $certificate->signatureAlgorithm; // returns the signature algorithm used to sign the certificate /** @var bool */ $certificate->isSelfSigned; // returns true if the certificate was self signed
Get raw certificate as JSON
$certificate->getRawCertificateFieldsAsJson();
Determining if the certificate is valid at a given date
Returns true if the certificate will still be valid. Takes a Carbon instance as the first parameter.
$certificate->isValidAt(Carbon::today()->addMonth(1));
Determining if certificate contains/convers a domain
Returns true if the certificate contains the domain
$certificate->containsDomain('joelmale.dev');
Please see CHANGELOG for a list of recent changes.
About
Easily retrieve the ssl certificate for any host