- Convert P12 to PEM using PHP and OpenSSL
- Convert P12 to PEM using PHP and OpenSSL
- IOS : How to convert .p12 file to .pem file using Terminal?
- How do I convert a combined PEM into a pkcs12 P12 file?
- How do I use OpenSSL in the terminal to convert a .pem file to other formats?
- Problem converting pkcs12 file into a pem
- https запрос при помощи cUrl на php
Convert P12 to PEM using PHP and OpenSSL
It’s also possible that OpenSSL is trying to read the config file, and doesn’t have permission to so, though it should give you an error about that. Question: I am trying to convert a client certificate from a pkcs12 type to a pem file using openssl, but this error is showed on my terminal.
Convert P12 to PEM using PHP and OpenSSL
I’m trying to convert some .p12 files in to .pem.
On my mac it works, with no interaction as i put the passwords in the code, but when i use this code:
system('openssl pkcs12 -clcerts -nokeys -out apns-dev-cert.pem -in apns-dev-cert.p12 -passin pass:'); system('openssl pkcs12 -nocerts -out apns-dev-key.pem -in apns-dev-key.p12 -passout pass:1234 -passin pass:'); system('openssl rsa -in apns-dev-key.pem -out apns-dev-key-noenc.pem -passin pass:1234'); system('cat apns-dev-cert.pem apns-dev-key-noenc.pem > apns-dev.pem'); My file permissions are 755. and for the passin the passwords were set to nothing so thats why they are blank. all the code here without the system() works in the mac terminal..
thanks for reading. hope you can help
$filename = 'apns-dev-cert.p12'; $password = '. '; $results = array(); $worked = openssl_pkcs12_read(file_get_contents($filename), $results, $password)); if($worked) < echo '', print_r($results, true), '‘; > else
Please try running this snippet. Set $password to whatever passphrase is needed to open the file. If there’s no password, set it to null. I don’t believe one is needed from your openssl commands.
You should get output with the desired private key, probably inside $results[‘pkey’] .
If you see your private key there, then you can pass it to openssl_pkey_export to get it in PEM format, which you can then write to a file:
$new_password = null; $result = null; $worked = openssl_pkey_export($results['pkey'], $result, $new_password); if($worked) < echo "It worked! Your new pkey is:\n", $result, '‘; > else
Set $new_password to your desired pkey password, if you want one.
This should work for you, based on what I’m reading on the various documentation pages.
If you really want to continue using the openssl command by shelling out, please consider using proc_open instead of system , so that you can properly catch error messages.
It’s also possible that OpenSSL is trying to read the config file, and doesn’t have permission to so, though it should give you an error about that.
Converting a Java Keystore into PEM Format, Suppose your keystore file is abcd.jks and its present at C:\Data, try this in cmd window, at the location where the file is present: keytool -export -rfc -keystore C:\Data\abcd.jks -alias abcd -file C:\Data\abcd.pem. Give password next, when prompted, and you will get the converted format at the location specified.
IOS : How to convert .p12 file to .pem file using Terminal?
iOS : How to convert .p12 file to .pe m file using Terminal? [ Gift : Animated Search Engine : https://bit.ly/AnimSearch ] iOS : How to convert . p12 fileto
How do I convert a combined PEM into a pkcs12 P12 file?
I have an Apple Push Notification Service pem file which I have working in a PHP script. I can send push notifications to iOS devices that have my app installed. I am trying to make it work with the APNS-Sharp project in my Mono environment. The APNS-Sharp library requires a PKCS12 P12 file and all I have is the PEM which has the certificate and the key combined.
How do I get my PKCS12 file from this?
Check this out: http://code.google.com/p/apns-sharp/wiki/HowToCreatePKCS12Certificate
Generate .pem file used to set up Apple Push Notifications, Now, open terminal write following command. Set terminal to the path where you have put .12 file. $ openssl pkcs12 -in yourCertifcate.p12 -out pemAPNSCert.pem -nodes Enter Import Password:
MAC verified OK Now your .pem file is generated. Verify .pem file … How do I use OpenSSL in the terminal to convert a .pem file to other formats?
I am trying to use OpenSSL in the terminal. I have installed OpenSSL using brew install openssl. I want to convert a .pem file to another format that my hosting provider will accept.
I have tried several different formulations of the code and plying the certificate from different places but none seem to work and all give me various error messages including permission denied.
This is what I tried last.
openssl pkcs12 -in /Users/myname/fullchain.pem -inkey /Users/myname/privkey.pem -out /Users/myname/fullchain.pfx -cacerts4552226412:error:0DFFF0A8:asn1 encoding routines:CRYPTO_internal:wrong tag:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22.250.1/libressl-2.6/crypto/asn1/tasn_dec.c:1125: 4552226412:error:0DFFF03A:asn1 encoding routines:CRYPTO_internal:nested asn1 error:/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-22.250.1/libressl-2.6/crypto/asn1/tasn_dec.c:306:Type=PKCS12What might this mean and what code should I be using?
Edit: I am getting output files but they are of course empty.
That error message is usually when the certificate format you pass to the command is not what it is expecting. The following command should solve it for you.
openssl pkcs12 -export -out /Users/myname/fullchain.pfx -inkey /Users/myname/privkey.pem -in /Users/myname/fullchain.pemIt should prompt you to enter an export password to encrypt the .pfx files content if it has succeeded.
How do you convert an unencrypted PEM file to an, 1 Answer. I believe this tutorial contains the information you are looking for, more or less, I believe you just need to remove the -passing part: $ mv test_rsa_key test_rsa_key.old $ openssl pkcs8 -topk8 -v2 des3 \ -in test_rsa_key.old \ -out test_rsa_key -passout ‘pass:super secret passphrase’. In …
Problem converting pkcs12 file into a pem
I am trying to convert a client certificate from a pkcs12 type to a pem file using openssl, but this error is showed on my terminal. Does anyone have any idea why this is happening? I haven’t edited or manually changed the p12 file. Even when I try to get some info from the .p12 file it shows error.
# openssl pkcs12 -in Desktop/cert.p12 -nokeys -out Desktop/cert-file.pem 139728018543680:error:0D0680A8:asn1 encoding routines:asn1_check_tlen:wrong tag. /crypto/asn1/tasn_dec.c:1130: 139728018543680:error:0D07803A:asn1 encoding routines:asn1_item_embed_d2i:nested asn1 error. /crypto/asn1/tasn_dec.c:290:Type=PKCS12Your cert looks like a PEM certificate which you are converting to PEM again.
Just edit the certificate by keeping only the contents between ——BEGIN CERTIFICATE—— and ——END CERTIFICATE—— and then try. It should work.
-----BEGIN CERTIFICATE----- MIIGJjCCBA6gAwIBAgIJAMDVkmXEzJzZMA0GCSqGSIb3DQEBCwUAMIGiMRUwEwYD YTESMBAGA1UEBxMJQ3liZXJqYXlhMSkwJwYDVQQKEyBJbmxhbmQgUmV2ZW51ZSBC b2FyZCBPZiBNYWxheXNpYTEqMCgGA1UECxMhSW50ZXJuYXNpb25hbCBUYXhhdGlv biBEZXBhcnRtZW50MB4XDTE4MDEwODEwMDk0M1oXDTQ2MDEyMTEwMDk0M1owgaIx FTATBgNVBAMTDGhhc2lsLmdvdi5teTELMAkGA1UEBhMCTVkxETAPBgNVBAgTCE1h bGF5c2lhMRIwEAYDVQQHEwlDeWJlcmpheWExKTAnBgNVBAoTIElubGFuZCBSZXZl AQDR1Ws2Wmao88RyDs6Mlc3IfEDTanGB6+93ppe94CcA/9nwgiOXMEuMaiu7oF2m /FMsu2vVoPpXnuqvtANoJsc7jcAXottvEF8sthibTOR98N++QHo9wbUl2uhfJzxK uEH3Pa0ekSAZN1I0EUdfOmn8lY0fui4QXr9s9TsavvHafx8/NrFaIiSNnKi3xKEg choMAap/zNeDUXf3Pio99rAaCBjHVI1ZEC7m4ve6G6J8715Zs5jf9AWieWhpg9Nk Si8Yqt/znKE4xdxNhIDkWIJHrsHoVpje5h01KatN5HIdW+dfxCcAHkD3ZiT5rV1u LEN9aNckWTzv8sbjCfKzOXogtQOizNhqwun0CHsujUhNOrI2cYlyda/0Ad8nHbm2 UiLCQvNQv5l81pjaB6oBdmwHIHZsLYCRxveWEjX2aSIl9Xt/al8fR2MM2nPmNIlF PjRfAGmL3kmABxqRmfj505AgQn9wagtL6O8zg32eoVwaZyJfis1K4lcuOpwOKFpz hm/2tkV22NuwropW8VHsxYTAqIbLkCMy+fH3R1cWOv8fDXqXtCGG3t1d5bUtmg6I CRlSYWGaJvP43dQc2QVReyq+lOs9y+EyK11rF1cRM6LEqOQ+fB0V5M8ftOcx0nQ1 J1iLGT10D3vyHVZh2Ab8iCkRq0kA2hihYI5Dc+ghuZGDWwIDAQABo10wWzAJBgNV HRMEAjAAMA4GA1UdDwEB/wQEAwIFoDAdBgNVHQ4EFgQUARc5dd5V+30sPQpNZ1aG ystXahAwHwYDVR0jBBgwFoAUARc5dd5V+30sPQpNZ1aGystXahAwDQYJKoZIhvcN AQELBQADggIBAGXow+tQOfsDj9M0aNmxZ2ivJrqZQXGEOYd2wi1t+um9uswug61J QIreVUn4xPMRoXVRtVbtc2xlHCbpmVhh5noVW4Y/Ym/2gMYpti3Ruta2N1PfPs8k G1yq4Bv5zIHAbU0j/EWYuYF9Oit4BEPfhLC33eFxtr49VBYPTacbrlOvXkd+Stxi FDnOdrOYL6qs1mB9boxfyB1sLijs2j4Ht5wz38j/1lQqDUJ4mfdZ2d9CGqc798l8 s13mECG4h9oj+MHgakpTci1nLnWRq/j01Cw/hq94jWCPwhEyMonnsWuG+EKNPTQ7 +OkJDDuen3jDGD4mlsN/vW5ILvqMfKhBNv+GdLI6hJGps7Eb7cAZ5ihfnoWdf+38 64tZWK07q9TJzo5asQ+2OdtcuuPVuPdBEC8eDtI0JpgKwX0PUxjsciXYwYFGAb3z xooszCvWH+MJ0zv3jWYbr1DtgWnTSumb8GlhPuF3t+vfOZ1enlYnrHiRaDCXRLOo t9yO0hsa9Sotz3Rbfc2MQuT9PRSW+2w8cTOtJZkh7QvX9q8TlwSENKRp -----END CERTIFICATE-----Convert SSL .pem to .p12 with or without OpenSSL, Using openssl, the command is openssl pkcs12 -export -in xxxx.pem -inkey xxxx.pem -out xxx.p12 -passout pas:newpassword -name «newname» I can run this from a terminal session and it works perfectly.
https запрос при помощи cUrl на php
Пользователи часто задают вопрос: как парсить сайты защищенные ssl сертификатами. У cURL для этого есть специальные средства. Сертификат подключается, как обычный файл плюс файл с ключами. Единственное ограничение: cURL на php понимает только сертификаты формата pem, а большинство серверов работает на связке p12+crt
Значит нужно найти конвертор.
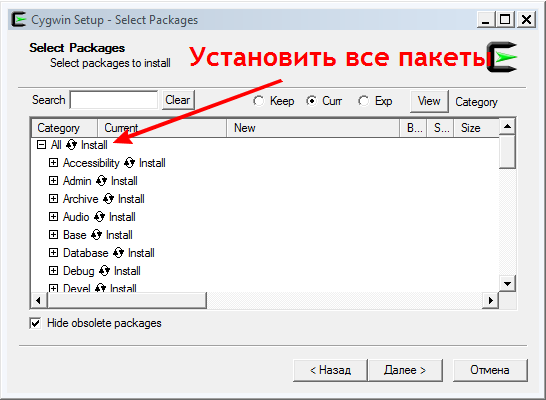
Для этого нужна библиотека openssl. Если у Вас linux, то она 100% у Вас уже стоит, и вы можете пропустить этот абзац. Для меня, как для windows пользователя, придумали специальные программы для запуска подобных пакетов. После недолгих поисков по сети я нашел cygwin. Если лень возиться с отдельной установкой OpenSSL и других попутных штук то лучше при установке кликните на установку всех пакетов.
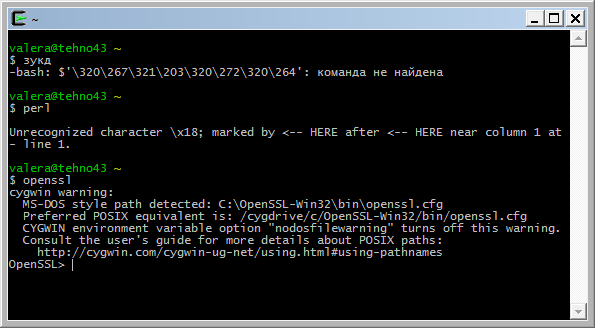
Пакеты грузятся довольно долго, но после установки всех пакетов Вам будет доступен вот такой терминал
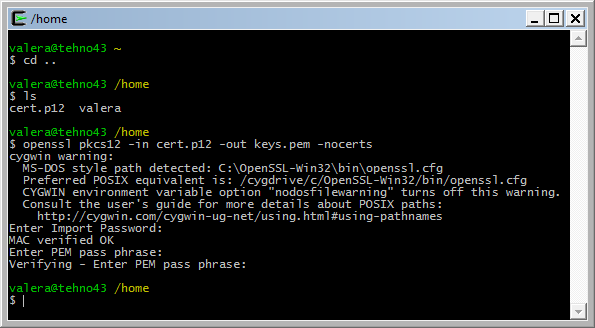
Берем файл *.p12 (его можно экспортировать из браузера) и бросаем его в папку C:/cygwin/home/
Далее в терминале с помощью команд cd . ls, cd переходим в папку home, если Вы еще не в ней, и запускаем следующую команду
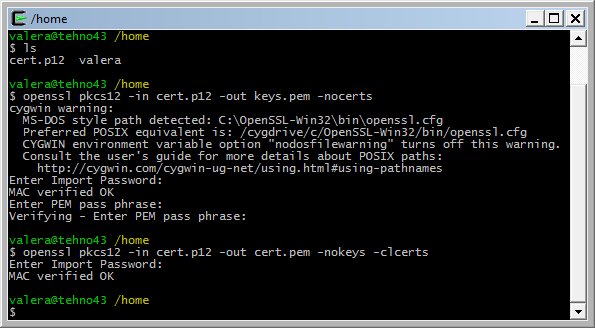
openssl pkcs12 -in file.p12 -out keys.pem -nocerts
программа попросит ввести пароль от сертификата. И другой пароль, который следует запомнить, к примеру 11111, затем повторить его.
Так мы сгенерировали файл с ключами. Теперь нужно сгенерировать файл с сертификатами.
openssl pkcs12 -in cert.p12 -out cert.pem -nokeys -clcerts
Нам потребуется еще один сертификат — сертификат сервера. Он имеет расширение crt, и отдается сервером при первом заходе.
Теперь у нас есть 3 файла. Создайте на своем веб-сервере файл index.php, рядом с ним положите эти три файла keys.pem, cert.pem и ca.crt
Вот так и парсим сайты со сложной системой защиты. На всякий случай предупрежу: не стоит парсить все подряд, ведь если ресурс защищен такого рода защитой, то там и сидят не дураки. Достаточно того, что сертификат, котороый у Вас есть уникален и по информации из него достаточно легко Вас идентифицировать. Поэтому сперва узнайте владельца домена, а уже потом предпринимайте различные действия. Ведь Вам будет очень неприятно, если вы проводя свои эксперименты с сертификатом своего банка, вдруг будете им забанены.
Будьте осторожны,желаю удачи.
Информация размещена лишь в ознакомительных целях, только для демонстрации технологии ssl+curl+php
Оставлять комментарии могут только зарегистрированные пользователи