- How to add or list certificates from keystore or trustStore in Java — Keytool Example
- Basics of SSL Certificates and Keystore in Java
- How to add, remove and list certificates from Java keystore
- Example of listing certificates from Java Keystore:
- Example of adding Certificate on Java KeyStore:
- Important points about SSL, KeyStore and keyTool in Java
- 9 comments :
- How to import a CA root certificate into the JVM trust store
- Instructions for importing a CA root certificate into the JVM trust store
- Step 1. Obtain the root certificate
- Step 2. Convert the root certificate to DER format
- Step 3. Validate the root certificate content
- Step 4. Import the root certificate into the JVM trust store
- Step 5. Verify that the root certificate has been imported
How to add or list certificates from keystore or trustStore in Java — Keytool Example
How to add certificates on keystore in Java is the primary question when you start working on SSL connection and a simple answer is keytool utility in Java is used to add or list Certificates into keystore. SSL is the industry standard for secure communication between two parties e.g. client and server. SSL offers two benefits, it encrypts data transferred between client and server to make it hard for someone to access and understand in between and SSL also verifies the identity of two parties in communication, and certificates are used for that purpose. SSL Setup in Java comes during various processes e.g. Setting up SSL on tomcat, configuring messaging over SSL, or JDBC over SSL are some examples of tasks where you need to deal with keyStore, certificates, and trust stores.
For those who are not aware of what is a keystore in Java and what is certificates, we will see a brief introduction in the next section, but for a more detailed discussion, you refer to my next post on how SSL, HTTPS, and Certificates work together in Java application.
And, If you are new to the Java world then I also recommend you go through The Complete Java MasterClass on Udemy to learn Java in a better and more structured way. This is one of the best and up-to-date courses to learn Java online.
Basics of SSL Certificates and Keystore in Java
When we access a secure site that uses SSL for providing identity and encryption, it provides a certificate that was verified by trusted third-party sites like Verisign , GoDaddy, or Thwaite . by using certificates browser or java clients know that they talking to the correct site (who it claims to be) and not on redirected proxy site.
This step is pretty transparent if you access websites using a browser because if the certificate is not on the browser’s trusted store it will ask you to add that certificate and it will be subsequently added, But when you access a secure site using Java program, this step of certificate handshaking is not transparent to user and certificates are verified from JRE’s trustStore. T
his trustStore is located on the JDK Installation directory referred by JAVA_HOME like JAVA_HOME/jre/lib/security and commonly named » cacerts «.
If the certificate provided by the secure site is present on JRE’s trustStore SSL connection would be established but if the certificate is not there then Java will throw an exception and to solve that you need to add that certificate into trustStore.
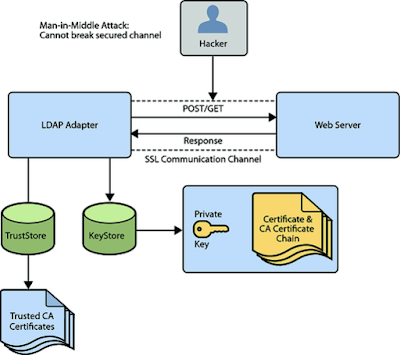
Terms like keyStore and trustStore are often used interchangeably and the same file can act as keystore as well as trustStore it is just a matter of pointing javax.net.ssl.keyStore and javax.net.ssl.trustStore properties to that file but there is a slight difference between keystore and trustStore.
A keyStore is used to store individual identity or certificates while a trustStore is used to store other parties’ certificates signed by CA. See the difference between keystore and trustStore, for more differences.
How to add, remove and list certificates from Java keystore
In this article, we will see how to add, remove and list certificates from the Java keystore using the keytool utility.
keytool is binary located inside JAVA_HOME/jre/lib/security folder and used for adding, removing, and listing certificates.
Example of listing certificates from Java Keystore:
Before adding new certificates in the keystore or trust store it’s good to see, count, and verify already installed certificates. run following keytool command to get a list of certificates from keystore:
javin @localhost : C / Program Files / Java / jdk1 . 6 . 0_26 / jre / lib / security keytool — list — keystore cacerts
Enter keystore password : changeit
Keystore type : JKS
Keystore provider : SUN
Your keystore contains 76 entries
digicertassuredidrootca , 07 / 01 / 2008 , trustedCertEntry ,
Certificate fingerprint ( MD5 ) : 87 : CE : 0B : 7B : 2A : 0E : 49 : 00 : E1 : 58 : 71 : 9B : 37 : A8 : 93 : 72
trustcenterclass2caii , 07 / 01 / 2008 , trustedCertEntry ,
Certificate fingerprint ( MD5 ) : CE : 78 : 33 : 5C : 59 : 78 : 01 : 6E : 18 : EA : B9 : 36 : A0 : B9 : 2E : 23
You see currently keystore » cacerts » holds 76 certificates. You can also see these Java Programming courses to learn more usages of keytool and other JDK command-line tools, and other Java fundamental concepts in a guided and structured way.
Example of adding Certificate on Java KeyStore:
1. Get Certificate: easier way is to point your browser to that URL and when the certificate is presented save it on your
2. Now go to the Security folder of your JRE installation directory. id you have JDK installed then it would be
Now this will print details about the certificate and ask you for confirmation of adding certificates:
if you cannot access a secure URL using the browser then you can use InstallCert by which you can add a certificate into keystore by the program. For detailed examples see the last section of LDAP authentication with SSL in Java and Spring security. I have provided detailed steps to use InstallCert.java tool.
Important points about SSL, KeyStore and keyTool in Java
1. Certificates are required to access secure sites using SSL protocol or making a secure connection from the client to the server.
2. JRE stores certificates inside keystore named as » cacerts » in folder C:/Program Files/Java//jdk1.6.0_20/jre/lib/security.
3. Common password of the keystore is » Changeit «.
4. Keytool is used to access keystore in Java and by using keytool you can list, add certificates from keystore.
5. If you are implementing an SSL connection on the Server-side say Tomcat you need both keyStore and trustStore, both can be the same file, though. keyStore will be used to store server certificates which the server will present to the client on SSL connection.
That’s all on how to add and list certificates from keyStore or trustStore in java. The keytool utility which comes with JDK installation will help you to create an alias, list certificates, etc.
9 comments :
Can you also let us know how to create keystore in Java, I mean what if I want to create a new keystore or copying data from one keyStore to another ? I am looking for exact command using keytool, please help.
I am getting this error while connecting to my Server using SSL in Java «javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed» Its says requested certificate not found. I am using self signed certificate created using keytool and I have imported that certificate into keystore. Is there any other way to install certificate ? do I need to install certificate on server side or only on client side ?
Instead of adding certificates using keyword tool, I prefer to use InstallCert.java utility. If you are adding certificates from website or url like LDAP URL, its best to use InstallCert.java. here is the command I use, just make sure to run this command from JRE/lib/security directory:
java -cp . InstallCert hostname:port
@Anonymous, There could be multiple reason of error javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed e.g.
1)Your trustStore may not contain certificates sent by Server for authentication.
2) You might not have provided trustStore using system property -Djavax.net.ssl.trustStore=, if you don’t provide an explicit trustStore than default trustStore which is jss2certs or cacerts and located in JRE/lib/security directory is used, which might not contain certificates sent by Server.
3) If your SSL Server is using Client authentication than you need to provide keyStore as well with System Property
-Djavax.net.ssl.keyStoreType=
-Djavax.net.ssl.keyStore=
-Djavax.net.ssl.keyStorePassword =
because on client side authentication SSL clients sends certificates corresponding to its public key to Server.
What you can do :
1) Check if you are using client side authentication or not, if not then you don’t need keystore, until you are SSL Server.
2) See whether you are using an explicit trustStore file or a default trustStore e.g. mytrustStore.jks in your application, make sure that you have Certificates to authenticate server on those trustStore.
One cal also use GUI based key management utility to create keystore and import certificates on that like IBM IkeyMan tool. Though I personally prefer keytool command which comes with standard Java installation, GUI tools are much easier to use. Another important thing to remember that, you can use same keystore as both trustStore and keyStore in Java which is used for different purposes.
Ikeyman is better when you want to create keyStore in Java, it support different kinds of keyStore e.g . JKS keyStore. Also if you want to create personal certificates, you first need to create certificate request and later signed it using A Signing authority e.g. GoDaday or Thwate. By the you can self sign your Certificate as well for development and testing purpose.
The default password of java keystore is «changeit», all in lower case.
hi . I get a problem installing certificate because of the computer is using automatic configuration script proxy when connect to internet. Some one can help to solve this problem ? thank you so much.
Hi,
I have .pem file and haven’t any alias and password. I am using jdk 8 with linux. I have import keystore with command keytool -import -trustcacerts -keystore /home/jdk1.8.0_60/jre/lib/security/cacerts -storepass changeit -file yourFile.pem and have imported successfully. When I am executing my code then I am facing this issue javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target. Please help me
How to import a CA root certificate into the JVM trust store
Web browsers and application runtimes, such as Java, have a special local database of recognised Certificate Authorities (CA). Each time an SSL/TLS connection is made, that database is queried in order to validate a server’s claimed identity (typically represented by its domain name).
If you try to make a secure connection (e.g. HTTPS or LDAPS) and the server doesn’t respond with a certificate issued by a recognised authority, the connection will fail with the following exception:
CertPathBuilderException: unable to find valid certification path to requested target If your company has its own CA, or, if you want to make SSL/TLS connections to a server in possession of a certificate issued by a CA which you recognise and trust, but is not listed in the default Java trust store, you will need to import the CA’s root certificate.
We recently encountered such a case when a user of the online OpenID Connect client was not able to connect to a web server which has a certificate issued by the StartCom CA. The root certificate of StartCom is recognised by browsers, but for some reason has not been included in the default JVM trust store.
Instructions for importing a CA root certificate into the JVM trust store
Step 1. Obtain the root certificate
For StartCom the root certificate was made available at http://www.startssl.com/certs/ca.pem, in PEM format. Certificates contain public information and CAs always make them available for download.
Step 2. Convert the root certificate to DER format
This can be done with help of the openssl toolkit, where ca.pem is the original certificate filename in PEM format, and ca.der the filename to output, in DER format (which the Java keytool utility can understand). If you were able to obtain the root certificate in DER format, skip this step.
openssl x509 -in ca.pem -inform pem -out ca.der -outform der Step 3. Validate the root certificate content
Ensure that the Java keytool can parse the certificate and display its content:
keytool -v -printcert -file ca.der Step 4. Import the root certificate into the JVM trust store
Enter the following command where $JAVA_HOME is a shell environment variable that points to your Java installation, e.g. to /usr/lib/jvm/java-7-oracle ; for -alias pick some unique name for the certificate in the store:
keytool -importcert -alias startssl -keystore $JAVA_HOME/jre/lib/security/cacerts -storepass changeit -file ca.der (the default password for the CA store is changeit )
The keytool will prompt you for confirmation, enter yes to complete the operation.
Step 5. Verify that the root certificate has been imported
To do that list the trust store content and filter for the certificate alias (name) with grep :
keytool -keystore "$JAVA_HOME/jre/lib/security/cacerts" -storepass changeit -list | grep startssl You will now be able to make secure SSL/TLS connections to servers which have a certificate signed by the CA which we just imported.