- LastPass 4.118.0 CRX for Chrome
- LastPass for Chrome
- More About LastPass
- Cracking encrypted Lastpass vaults
- What happened?#
- What can attackers do with the stolen vaults?#
- Lastpass Browser extension#
- Extracting encrypted vault#
- Lastpass SQLite database#
- Key value#
- Iteration count#
- Email#
- Formatted hash#
- Cracking Lastpass vaults with Hashcat#
- Useful Links and References#
- Chrome extension hdokiejnpimakedhajhdlcegeplioahd vault html
LastPass 4.118.0 CRX for Chrome
LastPass (hdokiejnpimakedhajhdlcegeplioahd): LastPass, an award-winning password manager, saves your passwords and gives you secure access from every computer and mobile device. Read More > or Download Now >
LastPass for Chrome
- • Type: Browser Extension
- • Latest Version: 4.118.0
- • Require: Chrome 18.0 and up
- • Offline: No
- • Developer: LastPass
- • Rating Average
- 4.37 out of 5
- • Rating Users
- 27499
- • Total Downloads
- 18072
- • Current Version Downloads
- 33
- • Updated: July 5, 2023
LastPass is a free Productivity Extension for Chrome. You could download the latest version crx file or old version crx files and install it.
Also LastPass is included in the following topics:
More About LastPass
Only remember one password — your LastPass master password. Save all your usernames and passwords to LastPass, and it will autologin to your sites and sync your passwords everywhere you need them.
«This robust password manager is a must-use free tool that supports multiple operating systems and browsers.» — PCMag Editors’ Choice
Save Everything:
— Store login usernames and passwords
— Checkout fast by adding credit cards & shopping profiles
— Attach docs, PDFs, images, audio, and more
— Save any piece of data you need to keep secure and easy-to-find
— Manage everything from a simple, searchable vault
— Add, edit, view, delete, and organize your passwords
Access Everywhere:
— LastPass is free to use on any computer, laptop, phone or tablet
— Install the LastPass browser extension on all computers
— Login with the same LastPass account everywhere
— Anything you save on one device is instantly available on all your other devices
— Download LastPass to all your computers and get our app for your smartphone or tablet
Improve Your Online Security:
— Generate secure passwords to replace weak ones
— Create new passwords as you sign up for sites
— Protect your LastPass account with multifactor authentication
— Use the LastPass security check to review your passwords and flag weak and duplicate passwords
Simplify your life:
— Never forget another password
— Generate strong passwords that you don’t have to remember
— Passwords are autofilled for you as you go to your sites — less typing!
— Securely share your passwords with friends and family
— Only worry about one master password
Only you know your master password, and only you can access your vault. Your master password is never shared with LastPass. That’s why millions of people and businesses trust LastPass to keep their information safe. We protect your data at every step.
Cracking encrypted Lastpass vaults
The recent (2022) compromise of Lastpass included email addresses, home addresses, names, and encrypted customer vaults. In this post I will demonstrate how attackers may leverage tools like Hashcat to crack an encrypted vault with a weak password.
In this post I will go into technical details on what attackers could do with the stolen encrypted vaults, specifically how they could use tools like Hashcat to crack vault passwords and get access to sensitive log-in credentials.
To simulate the stolen data, I will use my test Lastpass account to extract an encrypted vault from the Chrome Browser extension on macOS. Following this, I will use a wordlist attack to bruteforce the vault which has a weak and guessiable password.
Update: Fixed a few mistakes and added more clarification.
Update 2: More clarification on cracking section, added unencrypted URLs to the what was stolen section, and added a link to a Hashcat benchmark for Lastpass from 2013.
What happened?#
The Verge published an article which includes a great summary of the breach. There is also a blog post by Lastpass themselves. To summarise, in August 2022 Lastpass suffered a data breach where customer data and source code was stolen. Lastpass didn’t do a good job at letting the public (and customers) know of how bad the breach actually was.
What was stolen?
- a backup of customer vault data
- unencrypted website URLs
- company names, end-user names, billing addresses, email addresses, telephone numbers, and the IP addresses
- source-code and other intellectual property
What can attackers do with the stolen vaults?#
It really depends, there are a lot of things to consider. A few things that spring to mind are:
- How are the encrypted vaults stored in the cloud?
- Did a customer set a weak and easily guessed vault password?
- What is the key iteration (default or custom)?
- Other factors not covered?
And since I don’t know what the stolen data looks like, or how it may be encrypted, this blog post is only a theory and estimation based on data I have access to. This includes the SQLite database used by the Browser extension and data within it.
In the next sections I will demostrate how to extract the encrypted vault database from the Chrome extension and pull out specific information to start cracking with Hashcat.
Lastpass Browser extension#
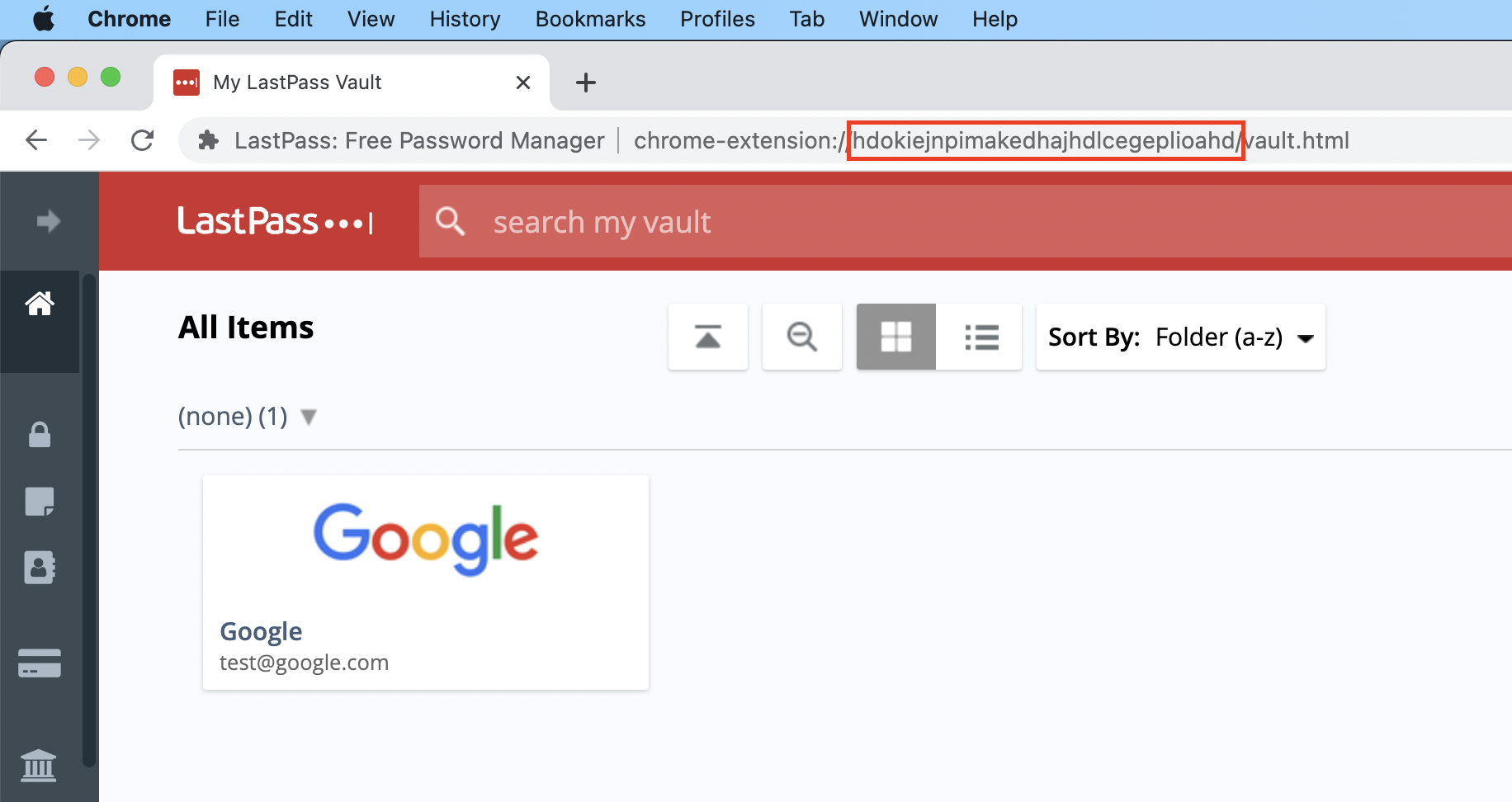
On Chrome Browsers each extension has a unique ID. The Lastpass extension uses hdokiejnpimakedhajhdlcegeplioahd as the ID. You can confirm this by visiting the URL chrome-extension://hdokiejnpimakedhajhdlcegeplioahd/vault.html in your address bar. You will be presented with the vault log-in page.
You can think of it as a local site that uses HTML and JavaScript within your Browser.
Extracting encrypted vault#
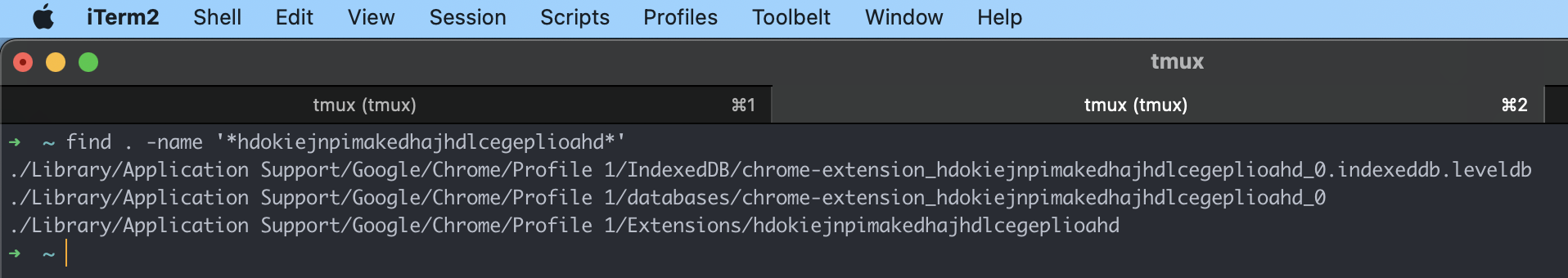
All extensions have their own folders which are stored locally on the system in various locations depending on OS.
As per online documentation the Lastpass support page states devices using Chrome Browsers on Windows systems store the vault data in the following PATH:
%LocalAppData%\Google\Chrome\User Data\Default\databases\chrome-extension_hdokiejnpimakedhajhdlcegeplioahd_0 On macOS systems the location is slightly different:
Note: I use two Profiles on Chrome, hence why you see Profile 1 instead of Default .
Lastpass SQLite database#
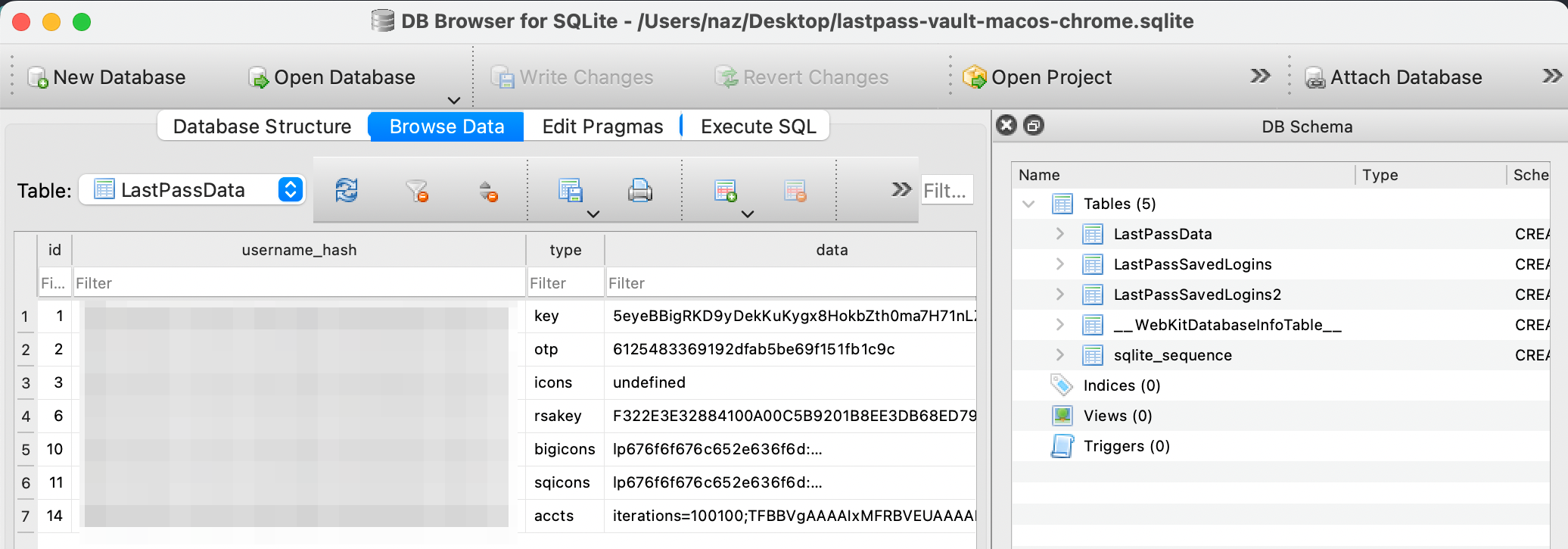
In this folder a SQLite file named 1 with the version: SQLite version 3039004 should be present. This is where encrypted vault data is stored and used by the extension.
➜ file 1 1: SQLite 3.x database, last written using SQLite version 3039004, file counter 21, database pages 22, cookie 0x5, schema 4, largest root page 11, UTF-8, vacuum mode 1, version-valid-for 21 You can then use a tool like DB Browser for SQLite to view the database contents. I also copied it to Desktop and renamed the file to lastpass-vault-macos-chrome.sqlite so it’s easier to remember.
All the interesting data is stored in a table called LastPassData .
To start cracking Lastpass vault passwords using Hashcat you need three things:
These need be formatted like so: KEY:ITERATION:EMAIL
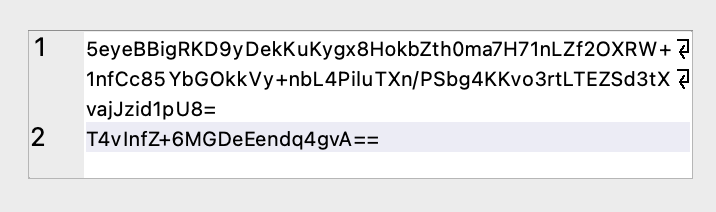
Key value#
To retrieve the key value, search column type where value key , and then in the data column select the second row e.g. T4vInfZ+6MGDeEendq4gvA== as shown below:
You can also execute the following SQL query:
SELECT substr(data, -24) FROM LastPassData WHERE type = 'key'; It is base64 encoded, which you can decode and get the hex value by:
echo "T4vInfZ+6MGDeEendq4gvA==" | base64 -d | xxd -p We now have the first requirement: 4f8bc89df67ee8c1837847a776ae20bc
Iteration count#
To retireve the Iteration count, search column type where value accts , and then in the data column the first few charaters before the ; . Lastpass changed the default iteration in 2018 from 5000 to 100100 .
You can also execute the following SQL query:
SELECT SUBSTR(data,0,INSTR(data,';')) FROM LastPassData WHERE type = 'accts'; We also now have the second requirement: 100100
Email#
The database contains a hashed email address value. But we do know that attackers already have this info since the recent Lastpass compromise included email addresses. For the purposes of this blog, I am not going to share the email address which I used.
Formatted hash#
With all the requirements the hash should look like this:
Cracking Lastpass vaults with Hashcat#
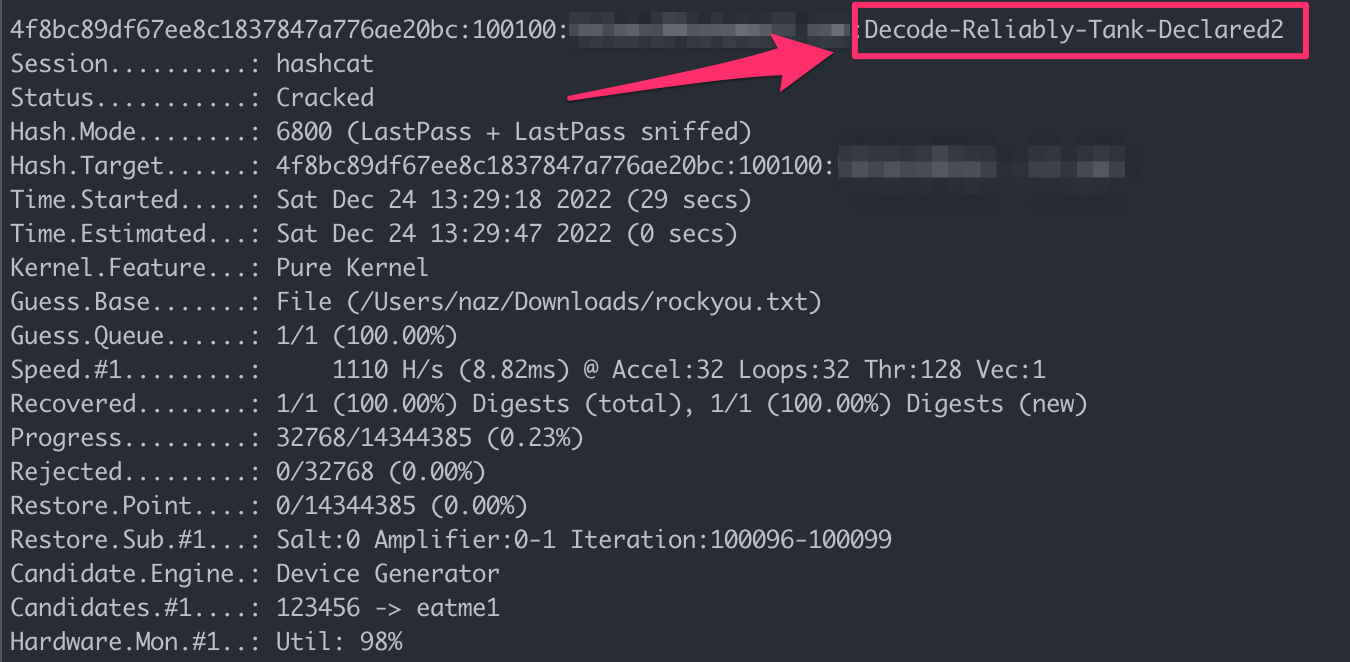
As a proof of concept I used my MacBook Air with the M1 chip to crack passwords. The speed was absolutely horrible 1110 H/s (hashes per second), but it did work. Attackers on the other hand can leverage multi-GPU device setups with optimised drivers that could easily reach speeds of 2,000,000+ H/s e.g. a benchmark from 2013.
As an example of bruteforcing vaults with weak passwords, I downloaded the popular rockyou.txt wordlist and put my actual vault master plaintext password inside (I was lazy and didn’t want to reset my password to a weak one), obiviously attackers can’t do this.
I then set the following Hashcat options:
hashcat -a 0 -m 6800 lastpass-hash.txt ~/Downloads/rockyou.txt - -a 0 attack mode Wordlist
- -m 6800 Lastpass hash algorithm
- lastpass-hash.txt hash formatted (KEY:ITERATION:EMAIL)
- rockyou.txt wordlist of plaintext passwords + my password
Note: This is only to demonstrate that the extracted values from above section do in fact correspond to the master vault password, you should ignore the time shown as it will take much longer than 29 seconds.
And there we have it, the master vault plaintext password successfully recovered.
Useful Links and References#
Chrome extension hdokiejnpimakedhajhdlcegeplioahd vault html
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- GoTo Community
- ›
- LastPass
- ›
- LastPass Support Discussions
- ›
- LastPass Chrome Extension opens new tab whenever I.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is annoying because it does not offer an option to change or disable it in the HotKey preference.
I work on Google Docs in a daily basis, where the same key combination means clear format. The LastPass extension is getting in the way.
RachelO
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you quit out of the LastPass mac app, are you then able to use the CMD+\ shortcut once LastPass is closed? If so, this may be a bug. So that our team can gather more details and hopefully resolve this, please submit a bug report following the steps here: https://support.logmeininc.com/lastpass/help/how-do-i-report-a-bug-to-lastpass
RachelO is a member of the LogMeIn Community Care Team.
Was your question answered? Please mark it as an Accepted Solution.
Was a post helpful or informative? Give it a Kudos!